SSO Module 4- Enhancing Online Security: Exploring 2FA, its Limitations, and the Menace of SIM Swapping
2FA improves security with two authentication types. Still, it faces risks from phishing, device loss, and SIM swapping. Countermeasures include offline 2FA apps, limited phone number sharing, hardware tokens, multi-signature wallets, and real-time transaction alerts.


In web3, ensuring robust security measures is paramount.
One such security is Two-Factor Authentication (2FA), which adds an extra layer of protection to user accounts and transactions.
In this course, we delve into the workings of 2FA in web3, examine its limitations, and shed light on the ever-growing threat of SIM swapping.
Understanding 2FA in Web3
Two-Factor Authentication is a security mechanism that requires users to provide two distinct authentication factors to access an account.
The aim being to secure as much as possible your funds by reducing the risk of something as simple as a password thief draining them in a blink.
These authentication factors fall into three categories:
- Something You Know: This includes a password, PIN, or security questions.
- Something You Have: A physical device, such as a smartphone or hardware token, which generates time-sensitive codes.
- Something You Are: Biometric data like fingerprints or facial recognition.
In the realm of web3, the most common application of 2FA involves combining a password (something you know) with a time-sensitive code generated by a smartphone app (something you have).
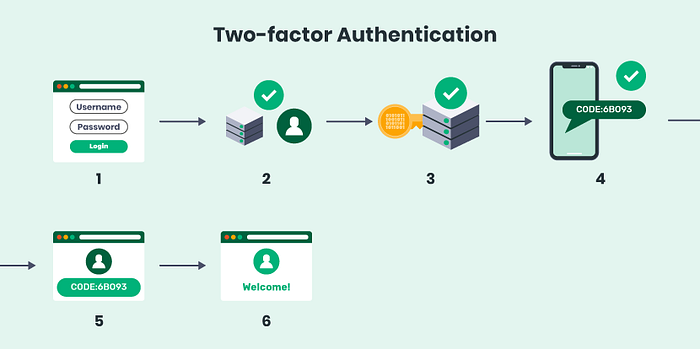
This dynamic code changes every few seconds, making it exceedingly difficult for attackers to gain unauthorized access, even if they’ve managed to obtain the password.
2FA are standard practices on Centralized Exchanges (CEXs), a must-go-through process as important as KYCing.
CEXs often develop their own “authenticator”, like Binance Authenticator that allows you to access your account through a QR code and a 16-digit key.
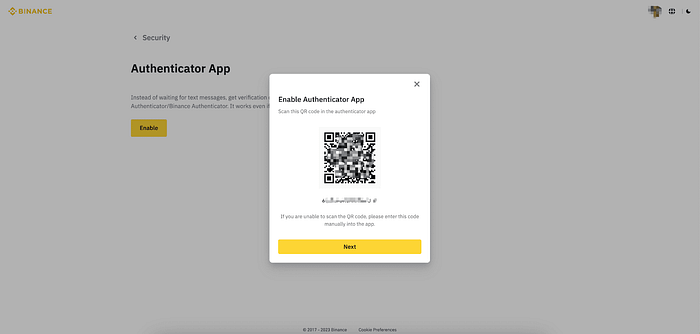
Limits of 2FA
Despite its effectiveness, 2FA does have certain limitations:
- Phishing Attacks: If users are tricked into revealing their credentials through fake websites or emails, 2FA might not entirely prevent unauthorized access.
- Device Dependence: Relying on a single device for 2FA could lead to a single point of failure. Losing the device or encountering technical issues can lock users out of their accounts.
- Social Engineering: Skilled attackers might manipulate customer service representatives into transferring a user’s 2FA to a new device, gaining unauthorized access.
The Threat of SIM Swapping
In the web3 space, SIM swapping has emerged as a significant threat.
SIM swapping involves a malicious actor convincing a user’s mobile carrier to transfer their phone number to a new SIM card under the attacker’s control.
Once this is achieved, the attacker can intercept 2FA codes sent via SMS.
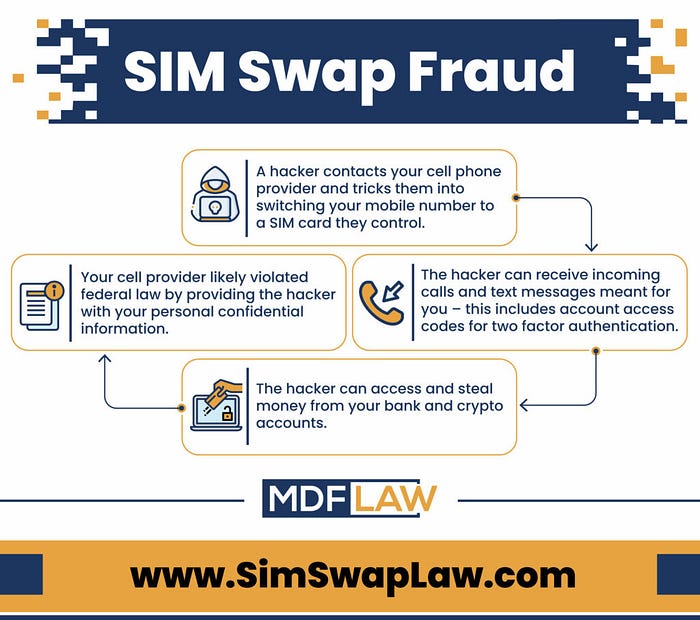
The implications of SIM swapping in the context of web3 are severe.
If an attacker gains control of a victim’s phone number, they can potentially bypass 2FA, gaining access to crypto wallets, dApps, and other sensitive accounts.
This has resulted in substantial financial losses for many individuals.
In 2018, crypto investor Michael Terpin fell victim to a staggering $23.8 million SIM swap attack. In October 2021, Coinbase revealed that cybercriminals had illicitly taken cryptocurrency from a minimum of 6,000 users as a result of a breach in their 2FA system, through sim swapping.
“As the popularity of Web3 grows and attracts more people into the industry, the likelihood of SIM swapping attacks also increases due to its relatively lower technical requirements.” recently told Blockchain Security Firm Slowmist CISO to the CoinTelegraph.
A slew of sim swapping attacks in the crypto space those past weeks proved those words true.
Since June 2023, more than 30+ crypto projects have been targeted by SIM swap attacks, that are used to take control of Twitter accounts and post wallet drainers. In a single attack, at least $765K worth of NFTs were stolen the Gutter Cat Gang twitter account was hacked through sim swapping.
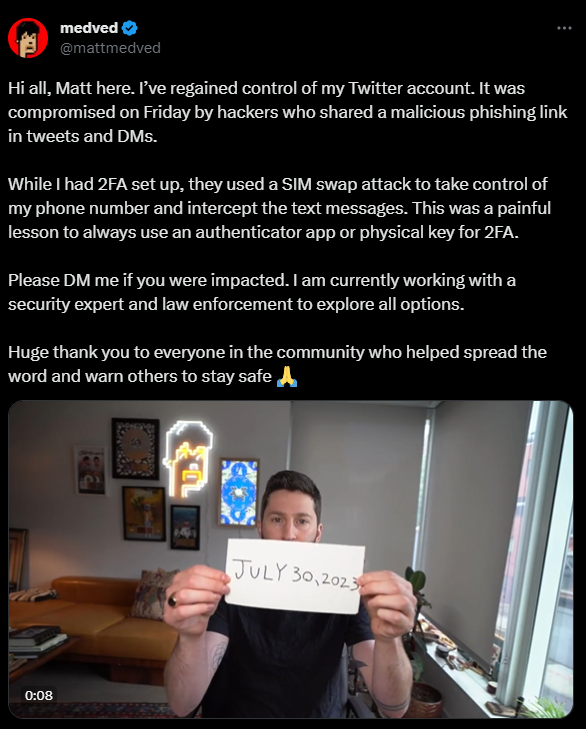
Mitigating the Threat
To counter the risks associated with SIM swapping and enhance security in web3, several steps can be taken:
- Authenticator Apps: Using dedicated 2FA apps like Google Authenticator or Authy generates codes offline, reducing vulnerability to SIM swapping.
- If you can’t be bothered to use an authenticator system outside of your phone number:
- You should at the very least disclose your phone number to as little people as possible and never on social media, including Linkedin. As well as protect personal data like name, address and date of birth, that can be used to retrieve your phone number.
- The best strategy that you can implement is to have a sim that is solely dedicated to authentificating you. Whose corresponding phone number is disclose to no one but you.
3. Hardware Tokens: Hardware devices like YubiKey provide a physical means of generating 2FA codes and are immune to SIM swapping.
4. Multi-Signature Wallets: Employing multi-signature wallets adds an additional layer of security, requiring multiple devices or parties to authorize transactions.
5. Transactions 2FA: At Nefture, we have developed a 2FA transaction system that alerts you of every transaction you make, ask for your validation and inform you of the potential risk(s) linked to it.
Through advanced algorithms that monitor transactions and identify potential risks in real-time, analyzes transaction patterns, blockchain data, and historical data to detect anomalies, fraudulent activities, and suspicious behavior, the user is forewarned of the risks involved for each transactions they wish to engage in and is able to take adequate actions in real-time.
In conclusion, while 2FA greatly bolsters security in the web3 landscape, its limitations and the looming threat of SIM swapping cannot be ignored.
To ensure maximum protection, users must adopt best practices such as using authenticator apps and hardware tokens.
As web3 continues to evolve, so too must our security measures evolve to counteract emerging threats and vulnerabilities.
Summary
Congratulations! You finished Module 4- Enhancing Security in Web3: Exploring 2FA, its Limitations, and the Menace of SIM Swapping
Let’s review your learnings:
2FA in Web3: Two-Factor Authentication (2FA) is a security method that uses two distinct verification factors for account access.
- Types:
- Knowledge (e.g., password)
- Possession (e.g., smartphone generating time-sensitive codes)
- Inherence (e.g., fingerprints).
- Application: In web3, a password combined with a dynamic smartphone-generated code is common.
Centralized Exchanges (CEXs) & 2FA: CEXs use 2FA widely. For instance, Binance has its own “authenticator” using a QR code and a key.
2FA Limitations:
- Vulnerable to phishing attacks.
- Device dependence: Lost or malfunctioning device could lock users out.
- Social engineering: Attackers might bypass 2FA through manipulative tactics.
SIM Swapping:
- Threat: Attackers deceive mobile carriers to transfer a victim’s phone number, thus intercepting 2FA codes sent via SMS.
- Impact: Bypassing 2FA allows unauthorized access to wallets, dApps, and sensitive accounts.
- Notable incidents: $23.8 million stolen from investor Michael Terpin in 2018 and a breach of Coinbase's 2FA system in 2021 affecting 6,000 users.
This article was brought to you by:


